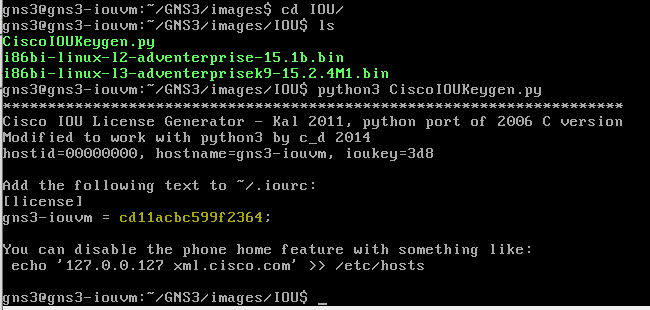
01. PC1 can ping to PC2 - Verified!
02. IPsec Implementation
IPsec allows exchanging of security protocols and encryption algorithms. Two configuration
elements are needed to implement IPsec VPN.
- Implement IKE and IPsec parameters.
• IKE P1 => define key exchange method used to pass and validate IKE policies btw peers.
• IKE p2 => peers exchange & match IPsec policies for authentication & encryption of data traffic.
IKE must enable to function IPsec. #crypto isakmp enable </enable isakmp on the router>
To allow IKE P1 negotiation => create ISAKMP policy and configure a peer association involving
that ISAKMP policy. ISAKMP policy defines auth:, enry:% & hash function used to send control traffic between
the two VPN endpoints.
When the ISAKMP security association is accepted by IKE peers, IKE P1 has been completed. IKE p2 will configure later.
03. Create ISAKMP policy
# crypto isakmp policy 10
Configure the ISAKMP policy on R1 & R3
hash => data integrity, not change the data
auth => packet get by the real peer
DH group => create a secret key shared by the peer.
# show cryp isakmp policy
04. Create pre-shared key # crypto isakmp key abc address 10.2.2.1 <peers IP address facing to other router>
05. IPsec TRANSFORM SET => router negotiate to form a security association.
# crypto ipsec transform-set 50 ?
# crypto ipsec transform-set 50 esp-aes 256 esp-sha-hmac
<ESP transfor with AES 256 CIPHER with ESP and the SHA hash function> The tranform set must match.
The function of IPsec transform set? it specifies the cryptographic algorithms and functions (transforms)
that a router employs on the actual data packets sent through the IPsec tunnel.
These algorith includes, encry: encapsu:auth: and data integrity service that IPsec can apply.
# crypto ipsec security-association lifetime seconds 1800
06. Define interesting traffic!!!
ACL => which traffic to encrypt. A packet that is denied by one of these ACL is not
dropped it is sent unencrypted. if there is no IPsec security association correctly configured, no traffic
is encrypted and traffic is forwarded unencrypted.
ACL
R1# access-list 101 permit ip 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.255
R3# access-list 101 permit ip 192.168.3.0 0.0.0.255 192.168.1.0 0.0.0.255
The ACL should be mirrored. otherwise not IPsec not form a security association.
07. Create and apply CRYPTO MAP
# crypto map CMAP 10 ipsec-isakmp
# match address 101 <which ACL>
# set peer 10.2.2.1
# set pfs group 5
# set transform-set 50
# set security-association lifetime seconds 900
# exit
# int e0/0
# crypto map CMAP
VERIFY IPSEC VPN OPERATION
R1#sh crypto isakmp sa
dst src state conn-id slot status
No output! because no interesting traffic has been identified.
PING from R1 to R2... this will not give an output cos
the interesting traffic means, if should obey to the ACL 101
which traffic from 192.168.1.0 network to 3.0 network.
Generate interesting traffic
R1#ping (enter)
target IP 192.168.3.1
source 192.168.1.1
....
R1#sh crypto isakmp sa
dst src state conn-id slot status
10.2.2.1 10.1.1.1 QM_IDLE 1 0 ACTIVE
R1#sh crypto ipsec sa
interface: Ethernet0/0
Crypto map tag: CMAP, local addr 10.1.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.3.0/255.255.255.0/0/0)
current_peer 10.2.2.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 40, #pkts encrypt: 40, #pkts digest: 40
#pkts decaps: 40, #pkts decrypt: 40, #pkts verify: 40
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 1, #recv errors 0
local crypto endpt.: 10.1.1.1, remote crypto endpt.: 10.2.2.1
path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/0
current outbound spi: 0xBBCDE611(3150833169)
inbound esp sas:
spi: 0x1608598B(369645963)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2001, flow_id: SW:1, crypto map: CMAP
sa timing: remaining key lifetime (k/sec): (4563839/326)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xBBCDE611(3150833169)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2002, flow_id: SW:2, crypto map: CMAP
sa timing: remaining key lifetime (k/sec): (4563839/325)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas: